Four-Layer Protection Against Domain-Based Threats
DefendDomain combines proactive domain monitoring, embedded security markers, content fingerprinting, and certificate monitoring to detect and prevent typosquatting, phishing, and brand impersonation before they impact your business.
The Four Protection Layers
Each layer provides unique detection capabilities that work together to create complete brand protection.
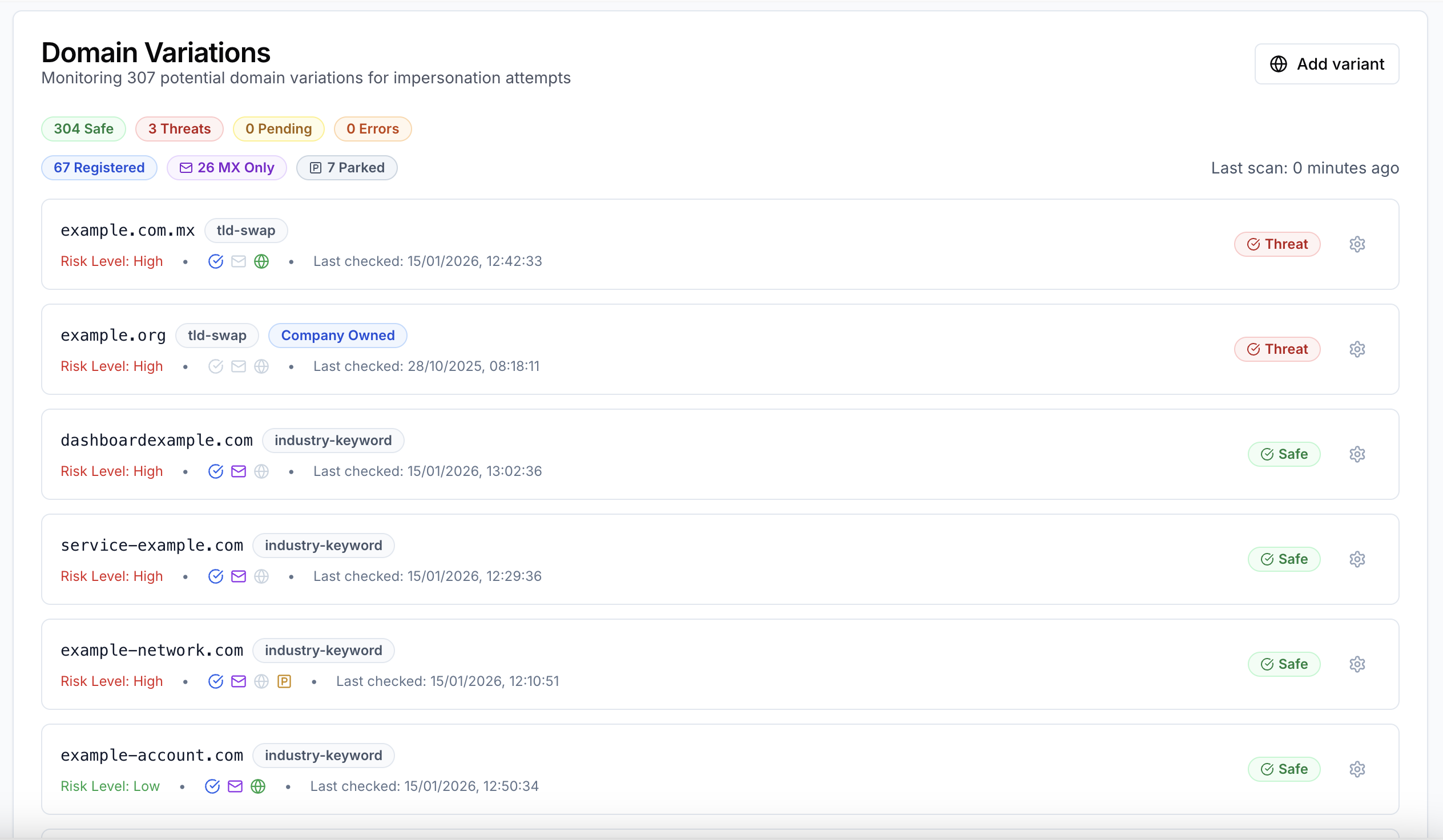
Proactive Domain Monitoring
Stop typosquatting before it becomes a threat
Automatically generates and monitors thousands of domain variations that attackers might register to impersonate your brand. Our AI-powered system uses 14+ variation algorithms to predict and track potential threats across 200+ TLDs.
- Character-level typos (substitution, deletion, insertion, transposition)
- Homoglyph attacks (Unicode confusables)
- Keyboard adjacency errors
- TLD variations (200+ TLDs)
- Industry-specific keyword combinations
- AI-generated contextual variations
Embedded Security Markers
Invisible protection that detects content theft in real-time
Embeds invisible tracking code on your website that alerts you when your content appears on unauthorized domains. Choose between JavaScript embeds or 1x1 pixel trackers with intelligent threat detection and zero false positives.
- JavaScript & pixel-based tracking options
- Advanced domain authorization (exact & wildcard)
- Multi-factor threat scoring algorithm
- Performance optimized (sub-100ms response)
- Comprehensive evidence collection
- Smart filtering (excludes iOS previews, CMS sandboxes)
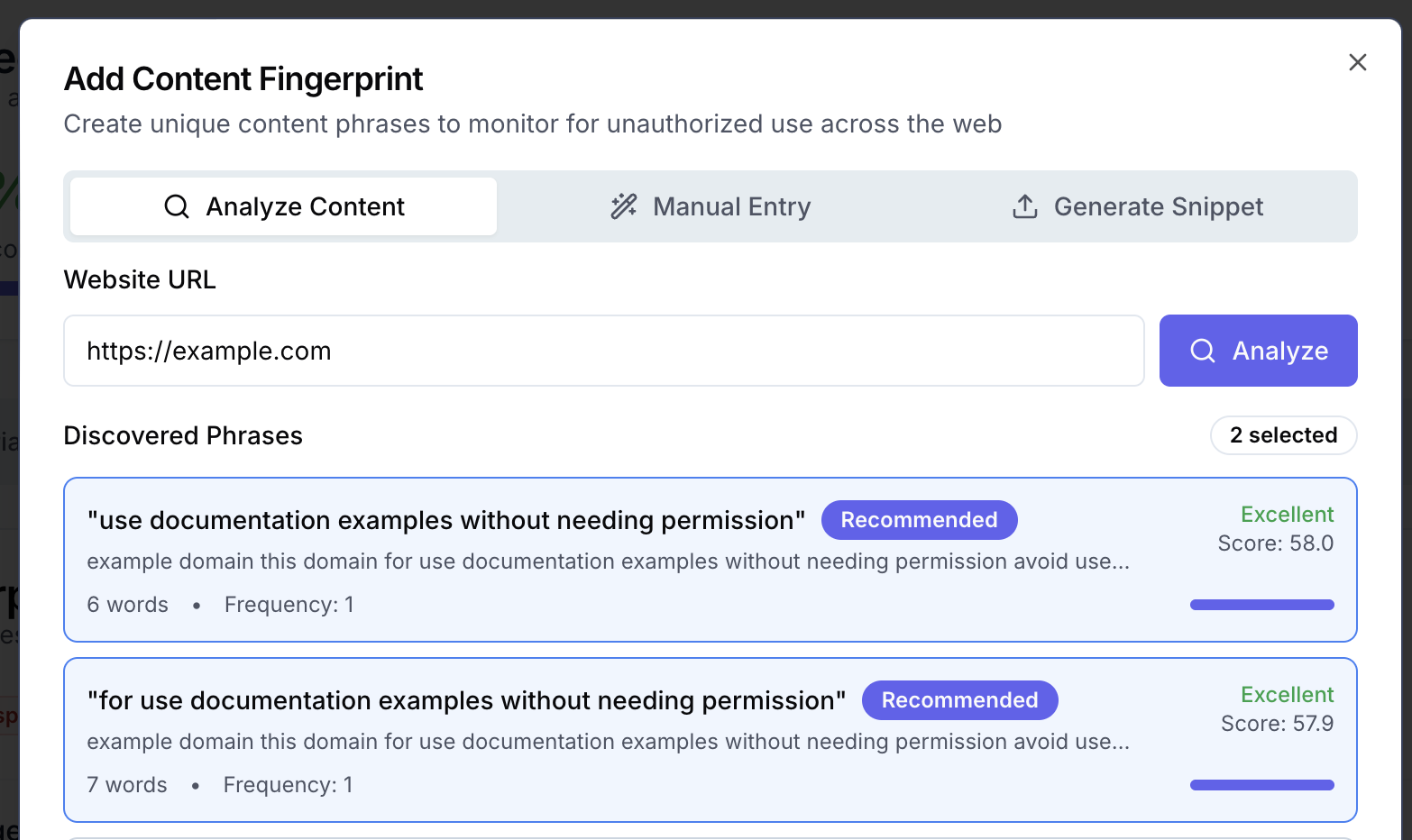
Content Fingerprinting & Search Monitoring
Find your stolen content anywhere on the web
Monitors search engines for your unique content appearing on unauthorized domains. Our AI extracts genuinely unique phrases from your site and continuously searches Google and Bing to detect content theft and impersonation.
- AI-powered phrase extraction & uniqueness scoring
- Three creation methods (URL analysis, manual entry, branded snippets)
- Google & Bing search engine monitoring
- Semantic analysis for paraphrasing detection
- Automated hourly verification
- Screenshot evidence collection
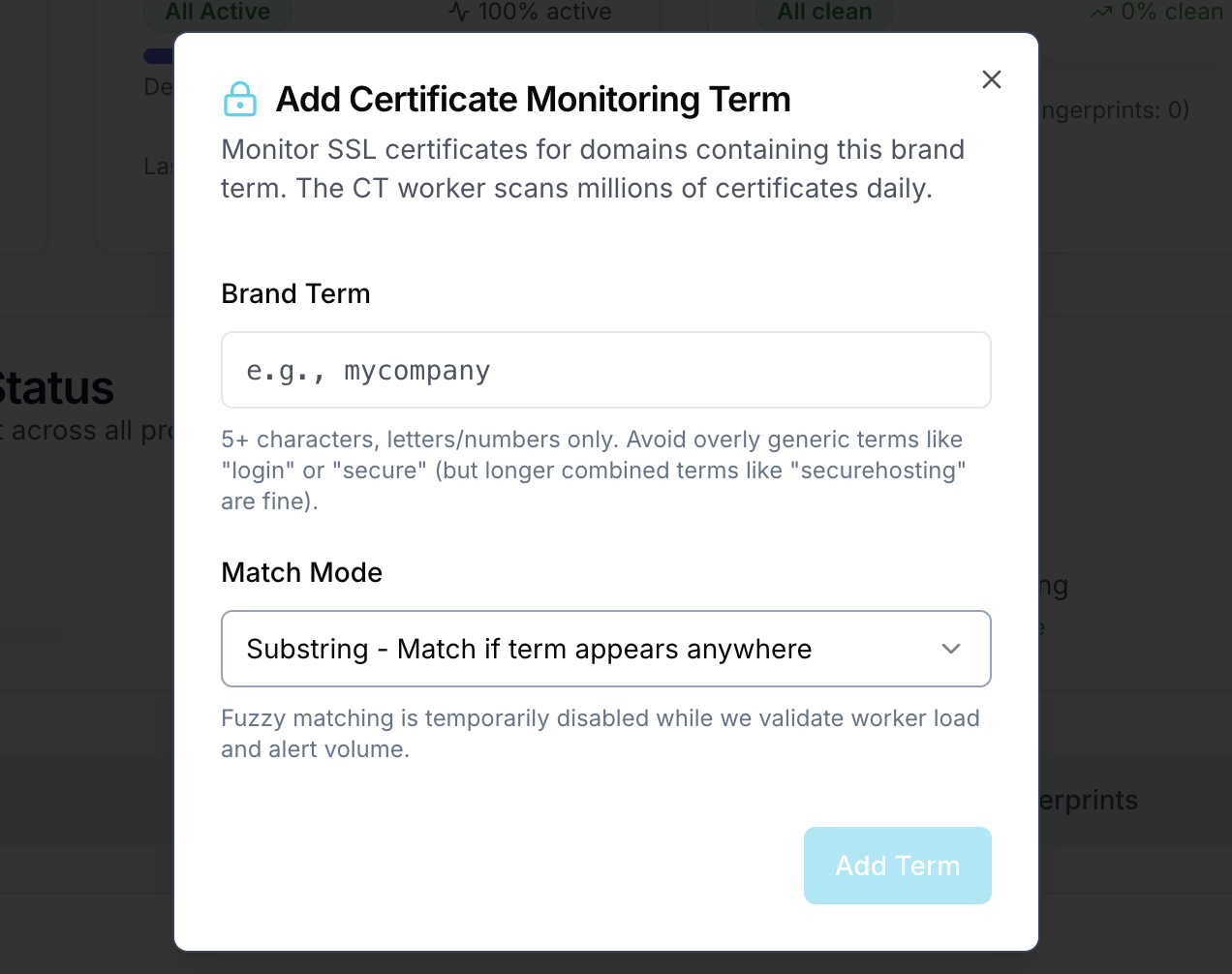
Certificate Monitoring
Real-time detection of SSL certificates impersonating your brand
Monitors Certificates being issued in real-time for domains impersonating your brand. Catch phishing sites the moment they get SSL certificates, often within minutes of issuance.
- Real-time Certificate monitoring across 75 sources
- Four matching algorithms (exact, normalized, homoglyph, fuzzy)
- False positive filtering & domain ownership verification
- Site liveness validation (DNS resolution)
- Distributed monitoring architecture
- Comprehensive evidence & certificate details
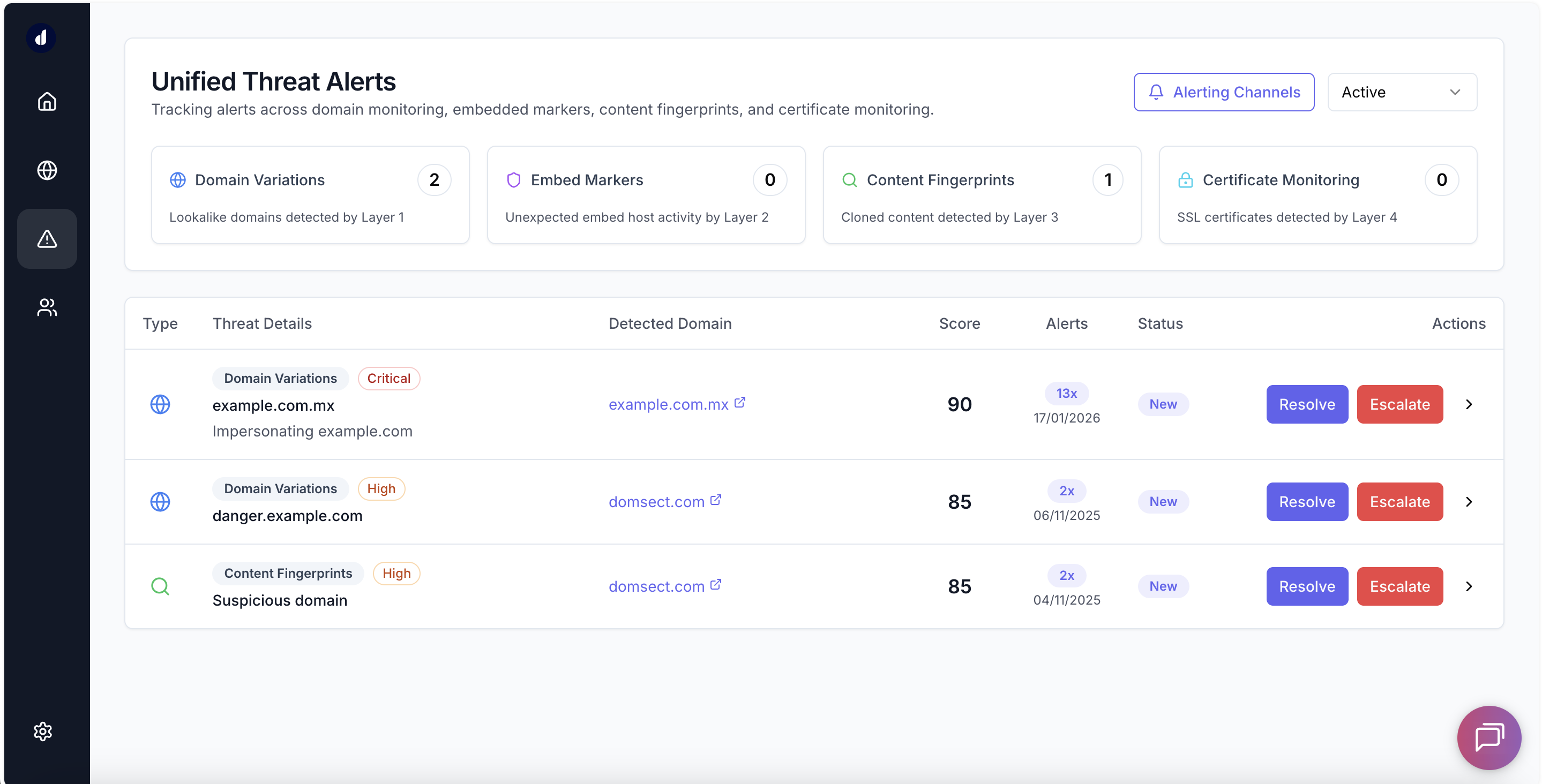
Unified Threat Management
One dashboard for all threats across all protection layers
Centralized Threat Detection & Response
Aggregates threats from all four protection layers into a single, actionable dashboard. Intelligent deduplication, threat lifecycle management, and comprehensive evidence collection ensure you can respond quickly and effectively to any threat.
Unified Dashboard
Single pane of glass for all threats with filtering by detection type and status
Intelligent Deduplication
Prevents duplicate alerts with exponential backoff for repeated threats
Threat Lifecycle
Six statuses from detection to resolution with full audit trail
Rich Evidence
Screenshots, WHOIS data, DNS records, and hosting provider details
Get Notified Where You Work
Flexible notification delivery to your preferred channels with securely encrypted credentials

Slack

Teams
Webhooks
SMS

Splunk HEC

Sentinel

Wazuh
Analytics & Insights
Real-time visibility into your security posture with comprehensive dashboards
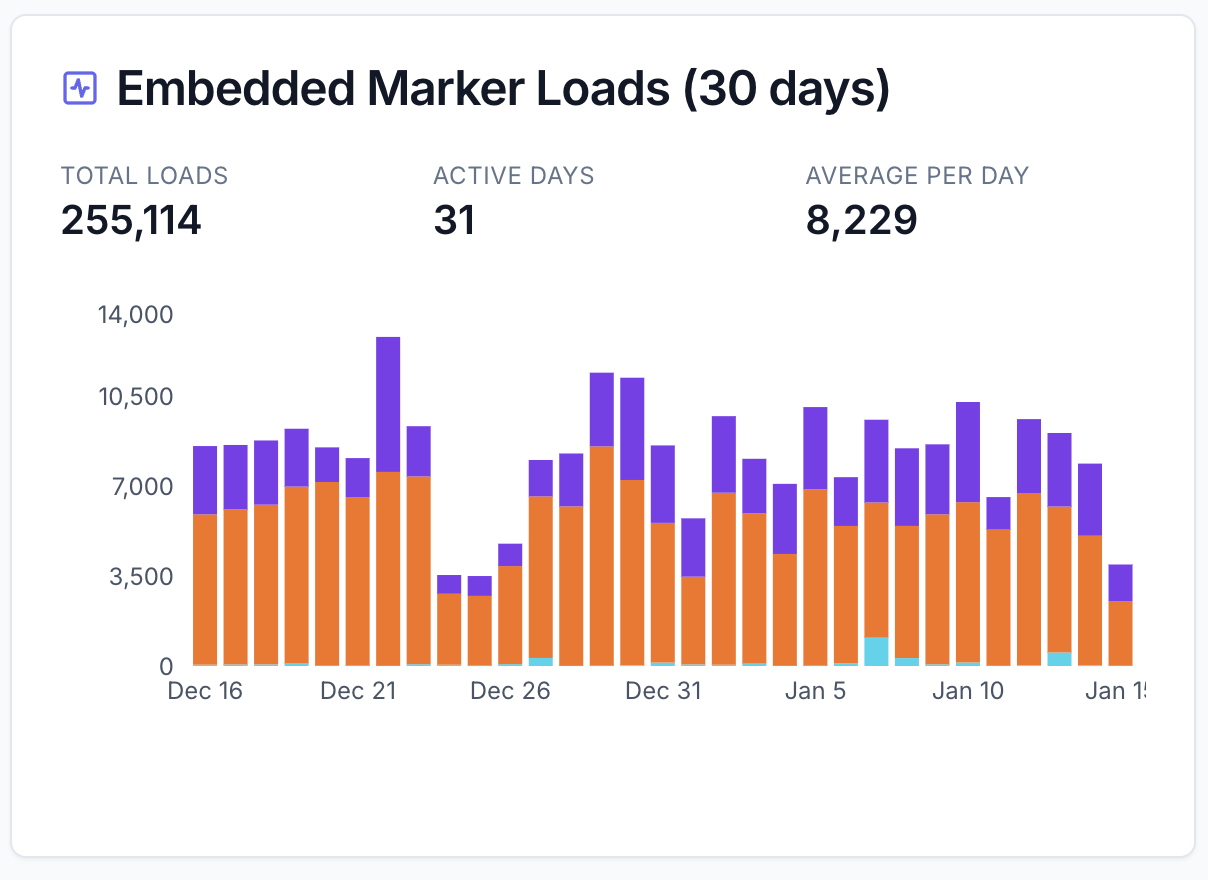
Security Overview Dashboard
At-a-glance security status with 30-day monitoring trends
- Protected domains count & active alerts
- 30-day activity chart across all layers
- Certificate monitoring statistics
- Team member count & company domains
Domain Protection Dashboard
Complete protection visibility per domain across all 4 layers
- Four-layer summary cards with scores
- Overall protection status badge (Excellent/Good/Warning/Critical)
- Last scan timestamps per layer
- Tabbed interface for each protection layer
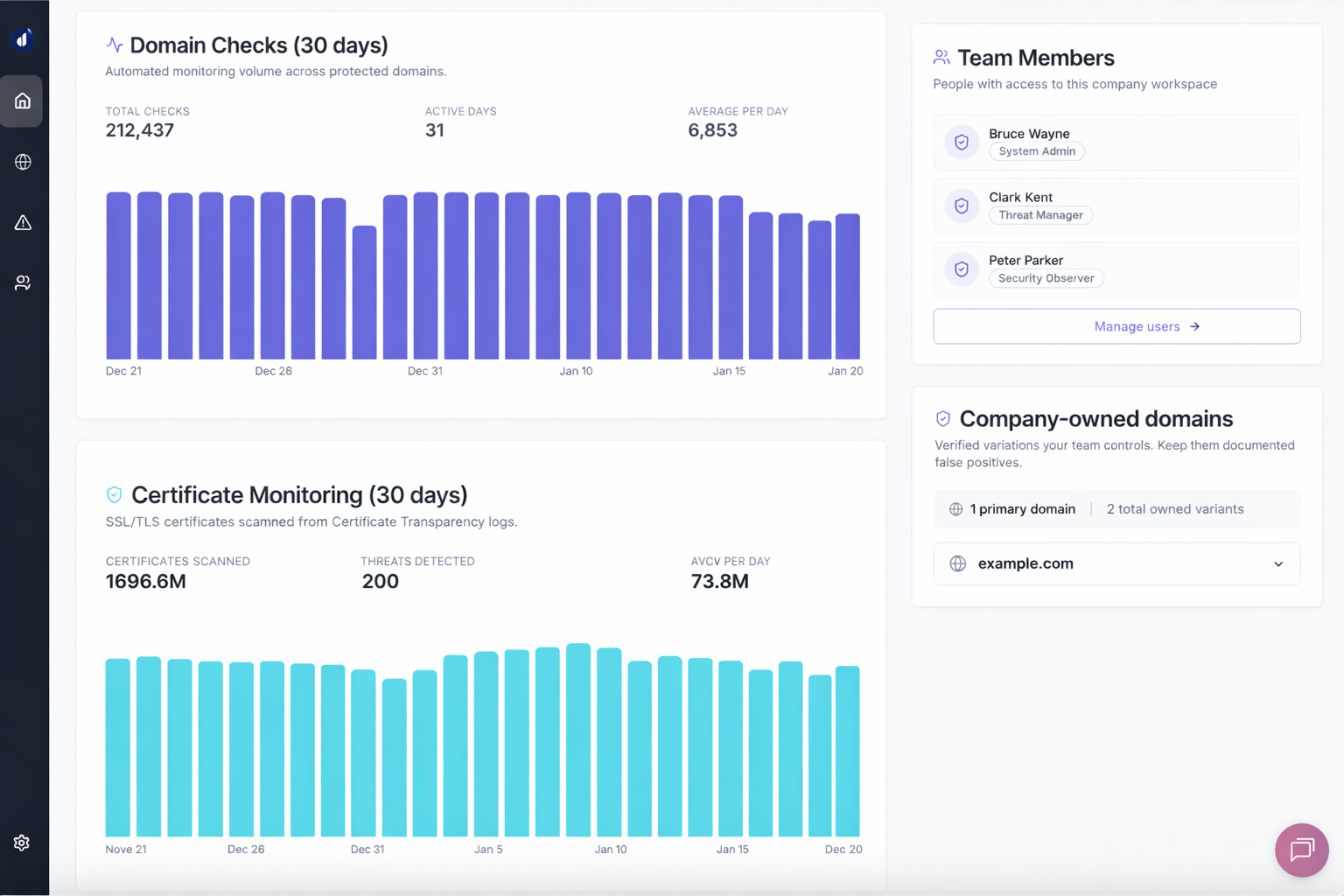
Team Collaboration
Secure, collaborative threat management with role-based access control and multi-company support.
Role Based Access Control
- System Admin: Full access, manage users and settings
- Threat Manager: Add domains, manage variations, respond to threats
- Security Observer: Read-only access to company data
Key Features
- Email-based team invitations
- Multi-company support (manage multiple brands)
- Row-level security (RLS) for data isolation
- Audit trail of team changes
Enterprise Ready
Scale protection across your organization with enterprise-grade compliance and integration features.
Compliance & Reporting
- ISO compliance reports for auditors
- Certificate of Protection (PDF documentation)
- Complete audit trails & evidence preservation
- Monitoring logs with execution metrics
API & Integration
- RESTful API for programmatic access
- Secure API authentication
- Custom webhook integrations
- SSO support (coming soon)
Built on Security-First Principles
Passwordless authentication, encrypted secrets, and comprehensive data protection
Passwordless OTP Login
- Magic link email authentication
- Rate limiting
- Timing attack protection
- No password management required
Encrypted Secrets Management
- Industry-standard encryption for sensitive credentials
- Webhook URLs & API tokens encrypted at rest
- Server-side only decryption
- Automatic encryption on storage
Row Level Security
- Company-scoped data isolation
- User-scoped data isolation
- Role-based access policies
- Service role auditing
Ready to Defend Your Domain?
Join leading organizations protecting their customers and employees from sophisticated domain-based attacks.
